ZTE Security: Pioneering Robust Information and Privacy Safeguards
ZTE is committed to keeping all information in its system private and secure. To implement this commitment, the company has instituted several safeguards, including a closed-loop management system and four classification levels for securing data. ZTE security has also outlined specific processes to mitigate any possible incidents. The text below will delve into these security measures and highlight ZTE’s exemplary standards for safeguarding information and privacy.
The Foundation of ZTE Security: A Closed-Loop Management System
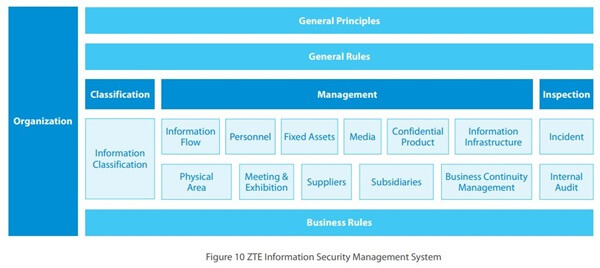
ZTE security uses two processes to manage information: hierarchical and closed-loop systems. In the hierarchical system, information is analyzed, and core assets are identified. The people, events, and other information-related topics and core assets are also analyzed to determine the best hierarchy for information flow. Information is classified, managed, and inspected. Inspections occur regularly to catch potential incidents and when an event occurs.
The closed-loop system allows for feedback to prevent any potential incidents and mitigate the impact of any events. The closed-loop system also helps to ensure compliance while making improvements within the system.
ZTE Security Practices: Safeguarding Data at Every Level
ZTE is committed to compliance with any and all local laws regarding data and privacy safeguards and also conforms to industry standards. ZTE places the utmost emphasis on protecting core data and personal information. This data includes that created by ZTE along with data collected and received by ZTE. It is generated both during production and operating processes. All data is classified into one of four groups: top secret, secret, internal use and public.
ZTE manages and secures data based on hierarchical grouping. Top secret data is data that is considered to cause a detrimental risk if breached. Secret data is data that would cause a significant risk if breached. Data classified as internal use does not pose a significant risk in the event of a breach, but it is not necessary for anyone outside of ZTE corporation. Public information is information that is available to everyone and poses no threat. Data may be associated with private, corporate, government and personal interests.
To protect each classification of data, ZTE employs a variety of encryption methods.
Global Recognition: ZTE’s ISO 27001 Certifications
ZTE’s compliance and commitment to security standards have helped it earn ISO 27001 certification. It is the first listed company in Mainland China to earn such certification. ISO is an accreditation association that sets the standards for safeguarding sensitive information and developing privacy best practices. Between 2005 and 2003, ZTE earned 27 ISO 27001 certifications, illustrating the company’s commitment to safeguarding privacy and information.
ZTE’s Privacy Protection Framework: Building Trust and Compliance
ZTE strives to comply with all regulations and policies. The company follows privacy protection regulations and laws of the country where it does business, making it a sound option for international dealings. Through compliance with local laws and regulations, ZTE aims to build joint trust between the company and its associates. ZTE also employs a strict code of ethics around privacy protection. This ethical standard further helps to build trust with other companies. ZTE thinks ahead when it comes to legal compliance and preventing any potential incidents.
ZTE constructs protection systems after careful consideration of risks and with the aim of being comprehensive. The company takes several factors into account, including systems, technology, organizations, and people. It regularly innovates as advancements are made and situations present themselves.
ZTE develops potential situations and incidents and then comes up with responses if something occurs. High-risk situations are conceptualized to put procedures into place to protect the data of ZTE’s associates, employees and users. ZTE employs three lines of defense to protect data in the case of an incident. Company policy includes procedures for responding to a data breach, managing data subject requests, transferring data across borders and complying with supplier regulations.
ZTE’s Commitment to Transparency and Privacy by Design
ZTE strives to be proactive when it comes to privacy matters. It is prudent to prevent incidents before they occur rather than waiting for an incident to find a solution. ZTE implements a Privacy by Design (PbD) process, which creates solutions for potential incidents during the design process of a product. By building solutions into designs, ZTE makes it easier to manage problems when they occur.
ZTE is also committed to transparency when it comes to all privacy measures. The company features all of its privacy procedures and safeguards at the Privacy Center on its website. This page keeps consumers, officials and business associates informed of ZTE’s latest privacy practices. The company aims to ensure that all involved parties are well aware of the measures places and understand how sensitive data is managed and used. The site also keeps users abreast of ZTE’s latest innovations and updates along with providing parties an avenue to submit feedback.
ZTE security has proven itself to be a leader when it comes to information and privacy safeguards. The company has robust procedures in place to deal with any security issues. ZTE builds safeguards into their products during the design phase. The company also ensures that all levels of data are properly managed and protected. ZTE will continue to set an example for companies that collect and manage sensitive information.



